n2n is a nice peer to peer vpn. Here are some hints, mostly so I’ll remember them.
There is a minor bit-o-confusion on the Macintosh. The edge nodes all use tun devices, rather than real ethernet devices, to plug in. You’ll need to install tun devices by hand. Then these devices will not show up in the various System Preferences. Don’t worry about that.
The n2n processes (both edge and supernode) will report status via UPD if you poke a UPD packet into at 127.0.0.1:5645 (aka localhost:5645) as so:
$ echo """" | ncat --idle-timeout 1s --udp localhost 5645
----------------
uptime 1212
edges 2
errors 0
reg_sup 21
reg_nak 0
fwd 0
broadcast 76
last fwd 25 sec ago
last reg 5 sec ago
Ncat: Idle timeout expired (1000 ms).
$
You will probably need to install ncat, which is part of nmap.
Each edge node in an n2n community’s pseudo ethernet needs a MAC address. Analagous to private IP addresses there are private MAC addresses. This mess will gin up a stable MAC address for your edge node based on the first mac address found on your machine.
N2N_FAKE_MAC=`ifconfig -a | awk '/ether/{print $2}' | head -1 | sed 's/^..:..:../10:00:00/'`
If you want an edge node to route all traffic thru you community’s VPN and then out to the rest of the network you need to do two things. Some edge node needs to volunteer to act as a gateway and each client that wants to use that gateway needs to configure their routing appropriately.
First, gateways typically run natd. Happily on the Mac you need only enable internet sharing in the sharing control panel to get that going.
Secondly, edge nodes that want to route over the VPN and out that gateway to the rest of the internet will then need to mess with their routing tables. That’s risky; mess up your routing table and you lose connectivity. You can find out what the default route for packets is by asking:
route -n get default
Note the result down since you’ll need it to switch back.
You can change the default route by doing (presume for a moment that your gateway node is running at 192.168.13.1):
route change default 192.168.13.1
But wait; that will break your N2N vpn, because your traffic to your peers will try to flow thru the new default. So you need to add specific routes to the supernodes and other edge nodes first. I don’t know how to get the list of edges; so I set them up by hand.
You switch back by resetting you default route, and tearing down the one off routes to other n2n nodes. Of course if, all else fails, reboot. Your on your own.
You can see the entire routing table by doing: “netstat -nr”.
 When traveling I sign up for Boingo’s wireless access, which later I then cancel.
When traveling I sign up for Boingo’s wireless access, which later I then cancel.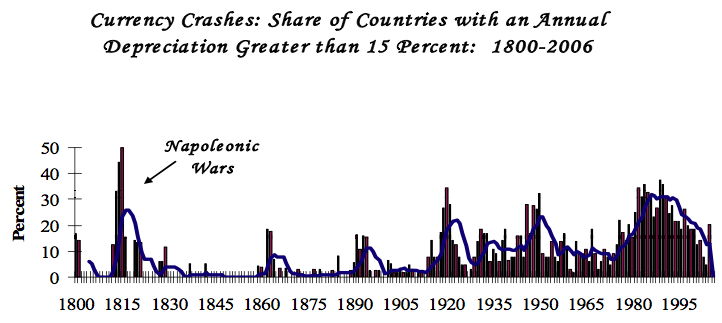
 I’m enjoying this
I’m enjoying this