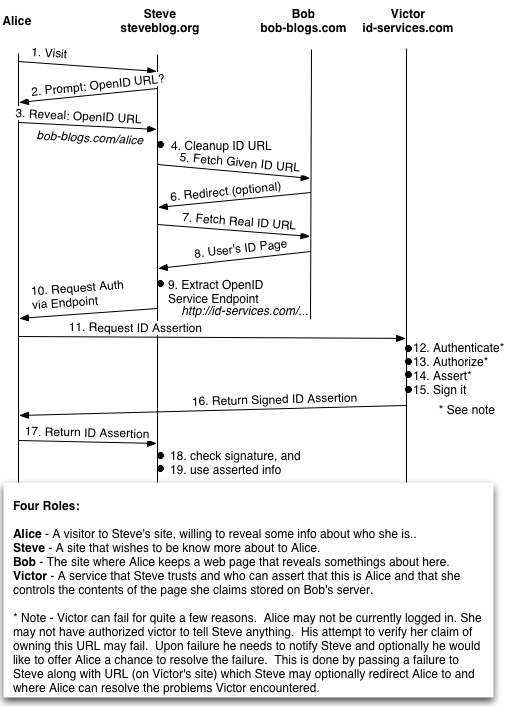
That drawing is, hopefully, an illustration of how OpenID allows a site, Steve, to authenticate a user, Alice. Steve asks Alice for here OpenID URL and Alice reveals that. Steve uses that to fetch the associated page, hosted at Bob’s. Information on that page tells him about Alice. For example that page could be Alice’s blog, or home page, or even just her public account.
To be sure that Alice’s claim to her page at Bob is valid Steve extracts from that page a pointer to a OpenID server. That server is run by Victor. Steve then asks Alices browser to obtain a signed assertion from Victor in support of her claim to the page. When Alice get’s the assertion she passes it back to Steve.
None of this requires JavaScript, but elements of it can be made to appear smoother by it’s addition.
This drawing does not show how Steve came to trust Victor, nor even how he came to be able to validate Victor’s signature on the assertion.
OpenID doesn’t say very much about the format of the page Alice reveals to Steve. The page is HTML, and it needs to have a link to the Victor’s service point. Of course Alice can reveal lots of information on that page. Pointers to FOAF files, ICMB links, VCards, what ever. That’s up to her.
The page that Alice reveals is very likely to be public. Steve does not have an account relationship with Bob. Similarly all this traffic is HTTP, not HTTPS.
Hopefully this is reasonably accurate.
Here is the scenario in words.
1. Alice visits Steve.
2. Steve prompts Alice for her OpenID URL.
3. Alice reveals here OpenID URL to Steve.
4. Steve cleans up the OpenID URL Alice Revealed.
5. Steve Fetchs the OpenID page Alice revealed from Bob.
6. Bob normalizes the OpenID URL and redirects Steve.
7. Steve fetchs the actual OpenID from Bob based on Alice
and Bob's input.
8. Bob returns Alice's OpenID page.
9. Steve extracts the OpenID service end point from that page.
10. Steve requests an assertion from Victor, via Alice, to prove
that Alice controls the OpenID page she claims.
11. Alice asks Victor for the assertion Steve wants.
12. Victor checks that it's Alice who's asking.
13. Victor, now working for Alice, checks that Alice has authorized telling Steve anything about her.
14. Victor creates the assertion Steve needs, checking of course that Alice controls this OpenID url.
15. Victor signs the assertion.
16. Victor sends that assertion back to Alice.
17. Alice sends the assertion back to Steve.
18. Steve verifies the Victor's signature.
19. Steve studies the assertion and acts approprately.
 Wikipedia is electing a board. Interesting example in the space of how to structure your goverance.
Wikipedia is electing a board. Interesting example in the space of how to structure your goverance. I’m such a sucker for charts like these. This one shows the amount of energy consumed per person in various nations or regions. Each dot is one year. You can see the US reacting to the energy crisis of the late 70s, and then once the supply recovered returning to form. (via
I’m such a sucker for charts like these. This one shows the amount of energy consumed per person in various nations or regions. Each dot is one year. You can see the US reacting to the energy crisis of the late 70s, and then once the supply recovered returning to form. (via