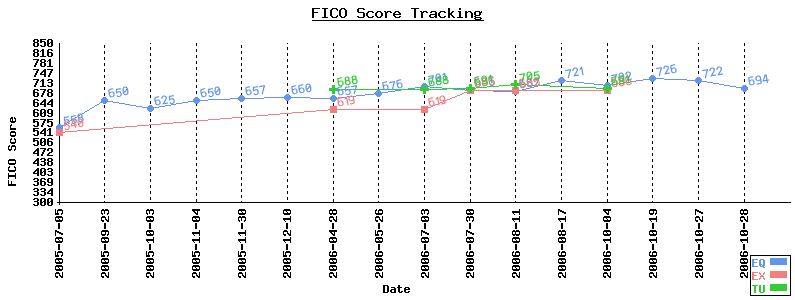
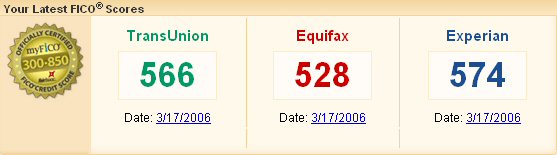
The HR department is administering the loyalty oath. This is annual event. We are requested to testify, via a form, to all our professional affiliations. To a degree I am, of course, joking. This invasion of our personal privacy is motivated by three concerns: concerns about possible conflict of interest (i.e. that the best interests of the employer might not be #1), concern that we might be not do what we are paid to do but rather work on some outside project, and finally that we might leverage the employer’s good name to the outsider’s benefit. I gleaned that list from the sections of the policy manual the form points to.
Social networks are a particularly interesting test case for looking at issues of the multihoming since of course they are where you make you home. I have account memberships in about a half dozen different social networking sites; but I don’t actually participate in any of them. Though that all depends on your definition of social networking site. If your more generous in your definition, including say all the on-line forums and mailing lists that include a social (v.s. purely on-topic) component then the number of sites I have accounts at explodes. A quick review of my password wallet suggests the number gets up toward a hundred; the phrase ‘a gross’ seems useful at this point. An then some percentage of the blogs I read have a social (or community) subtext.
Some of these places are quite social. The shaving and diet forums for example. The Oil Drum and Crooked Timber are two nice examples of blogs that sustain a community around them. Others are semi-social; the one for my PDA for example. It’s worth noting in passing that the social can make it a bit tough to keep the sites useful for their nominal on-topic purpose.
Where you sit changes how you look at the question of multihoming and social networking sites. If you have a large stake in one; owning LinkedIn for example but even if you have invested a lot of your social energy into a particular one your profession for example, then you are likely to be interested in ways of reducing the degree of multihoming. There is certainly plenty of literature on how to execute on that.
Lots of people interested in knowledge flows have noticed that that individuals that cross between two social/professional networks often account for critical knowledge transfers. So if your interested in encouraging that kind of thing then you might be interested in how to manage and enable increased multihoming. I don’t think I’ve ever worked for employer who failed to consciously, though rarely conscientiously, encourage a modicum of that kind of thing.
Multiple social networks create some diversification, which in turn can be a buffer against various risks. Two risks bear mentioning. If a social network goes bad having other networks enables members to exit, but also it enable them to be critical and that critique can be key to fixing what going wrong. Having multiple social networks also allows members to take risks, not just of criticism, but also to take risks that may do irredeemable damage to their reputation; such risks are much harder to take if there no other network to retreat into.
None of this helps to puzzle out the question of exactly how many of my ‘professional’ associations I should enumerate on this form. I’m sorely tempted to enumerate the complete list of all the on-line forums I’m a member of to which I both feel some loyalty and have any overlap with my employer’s vast range of activities. Just for fun. Oh, but curiously I appear to be in a job category where they decided to wave the requirement. Well golly, now my feelings are hurt – they don’t seem to care if I’m a two timing disloyal abuser of the brand!