 This is a long rambling post about an authentication trick I’ve not observed used in the wild. But it’s analagous to two tricks often observed in the wild. This trick is a way to do authentication. It is a hybrid of the web bugs, used by firms to build models of user behavior, and the trick of creating personalized Ads. Like Amazon does for it’s donation buttons.
This is a long rambling post about an authentication trick I’ve not observed used in the wild. But it’s analagous to two tricks often observed in the wild. This trick is a way to do authentication. It is a hybrid of the web bugs, used by firms to build models of user behavior, and the trick of creating personalized Ads. Like Amazon does for it’s donation buttons.
Here’s the scheme. All authentication schemes sooner or later work by having some third party vouch for the user. At that point there are always, at least, three parties in the game. The user who wishes to be authenticated. The site that wants to get to know him. And finally the third party that already knows the user and who the curious site also trusts.
 Lots of third parties get used for this. Paypal has a trick where they satisfy their curiosity by depositing some pennies into your bank account and then you prove that it’s your account by telling them how many pennies they deposited. They also get you to reveal your bank account data as a bonus.
Lots of third parties get used for this. Paypal has a trick where they satisfy their curiosity by depositing some pennies into your bank account and then you prove that it’s your account by telling them how many pennies they deposited. They also get you to reveal your bank account data as a bonus.
Google recently adopted the trick of sending a SMS message to your cell phone. As an added bonus they get you to reveal you cell phone #.
The most typical technique is to have you reveal your email address and then the curious site sends you an email and you prove that is in fact your email address.
The bank, the cell phone company, the email address provider are filling the role of third party that can vouch for you. Of course these are more or less trustworthy. Any third party with a ongoing relationship might fill this role. You library, you government, your ISP, Amazon, Yahoo, Google, your OS vendor.
So here’s the trick. Any of these could offer a service to curious sites. When you go to set up a new account the curious site could place a web bug or larger image on account set up page.
The trick involves what we put into that image. What if we put a one time pin into that image? The user then copies the pin from the image into the account sign up page. The site he’s signing up with then takes that data and queries the 3rd party site to setup the account.
Of course a firm like DoubleClick can offer fraud protection services without the bother of getting permission from the user, and they could use web bugs to do that. But the key thing here is that the user is explicitly in the loop, he is implicitly granting permission for the trusted third party to help with authenticating him as he sets up the account.
Notice one key thing. While in the examples above the users bank account, cell phone #, or email address was revealed to the curious site. In fact the higher the level of trust the 3rd party enjoys the more serious the bit of information revealed. This scheme breaks that pattern. The 3rd party doesn’t need to reveal anything beyond the fact that they know the user. They don’t have to give up any account data. The user can remain pretty close to anonymous. Of course if more information needs to be revealed that can be arranged.
This scheme is slightly analagous to OpenID. In that system users are prompted by the curious site for their OpenID url. The site then uses that to fetch a page of info about them, and on that page is a pointer to a 3rd party that can vouch for them (well vouch that they control the page in quesiton). But actually this is quite different because the OpenID design forces the user to reveal a universal identifier, i.e. his OpenID url. While this system requires only that the user admit he has a relationship with the the trusted third party.
This is also analagous to the common scarab systems where a site places a branded scarab on their page and the user is encouraged to click on it to authenticate. These scarabs don’t need to be web bugs and usually aren’t. So unlike the Amazon donation scheme only the third party’s brand appear on them and nothing showing how the third party recognizes this users.
Scarab schemes didn’t gain traction in the market. The curious sites hated them because the threatened their customer relationships. The scarab vendors, like Passport, looked like they would stick their nose into the middle of the relationship. One term used for that entanglement is “account linking” the authentication site and the curious site both have account relationships with the user and part of the design for most of these systems involved linking these accounts. Another way to describe the fear that the scarab vendors would intrude on the the relationship of the curious sites is to say that they feared that one account would become subordinate to the other one. For example that before the user could get to his eBay account he would need to pass thru his dominate Passport acount.
The scheme outline here involves no account linking at all. The in this scheme the trusted third party X is only providing a single service – a means for the user to prove to the curious site that he has a relationship with X. That’s it. That’s less likely to threaten the curious sites.
The point of all that is that we reduce the threat to the user and the curious site.
This is also analagous to the capcha schemes. They present a puzzle to the user that by solving increases the site’s confidence that the user is a human. In this case we are asking the user to prove he has a sufficently high quality relationship with a third party site. Since such relationships are, presumably, difficult to obtain – i.e. they take time.
While there are two things I like about this scheme – very little is revealed about the user and no long term account linking is done – it is tempting to do a modicum of durable linking.
After the user enters the pin presented to him the curious site then queries the trusted site to see if that pin is valid. The trusted site can reply yes, no, or it might send back something more complex. Anything more complex implies either more revealing or more linking.
If the third party site hands back a token representing the user that allows further transactions about that user. For example if the curious site uses this to prevent spam his blog that token could be used later to report a spam event back to the trust site. that seems like a fine use. Of course it could also be used to send back more private or slanderous info about the user.
Tokens like the one in that example are common in account linking designs. They denote the linking.
Meanwhile if you suffered thru this entire thing I’m amazed! But here’s an amusing variation on this idea. How about a scheme were you can only comment on a blog if you make a small donation to one of the set of charities selected by the blog’s operator.


 Steve has a
Steve has a  This is a long rambling post about an authentication trick I’ve not observed used in the wild. But it’s analagous to two tricks often observed in the wild. This trick is a way to do authentication. It is a hybrid of the web bugs, used by firms to build models of user behavior, and the trick of creating personalized Ads. Like Amazon does for it’s donation buttons.
This is a long rambling post about an authentication trick I’ve not observed used in the wild. But it’s analagous to two tricks often observed in the wild. This trick is a way to do authentication. It is a hybrid of the web bugs, used by firms to build models of user behavior, and the trick of creating personalized Ads. Like Amazon does for it’s donation buttons. Lots of third parties get used for this. Paypal has a trick where they satisfy their curiosity by depositing some pennies into your bank account and then you prove that it’s your account by telling them how many pennies they deposited. They also get you to reveal your bank account data as a bonus.
Lots of third parties get used for this. Paypal has a trick where they satisfy their curiosity by depositing some pennies into your bank account and then you prove that it’s your account by telling them how many pennies they deposited. They also get you to reveal your bank account data as a bonus.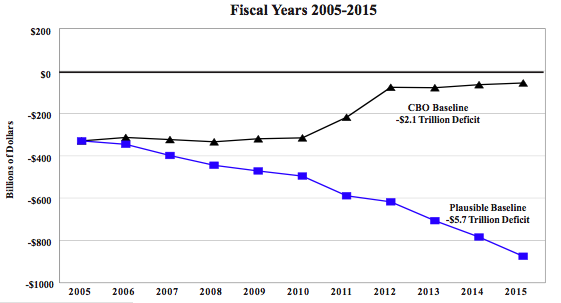
 Artist trading cards are the size of a baseball card. Artists make them to trade with each other. Some are just
Artist trading cards are the size of a baseball card. Artists make them to trade with each other. Some are just