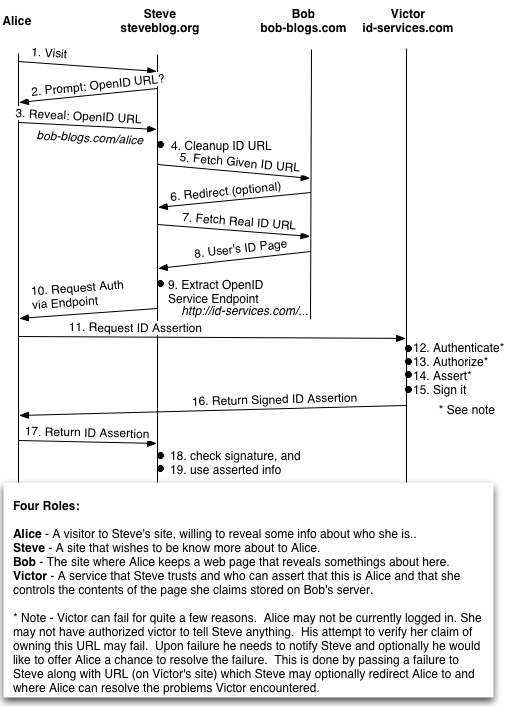
OpenID’s #1 feature is the decision to have a web page for every persona. For example my OpenID might be “enthusiasm.cozy.org” (well actually it’s https://enthusiasm.cozy.org/ but OpenID sanctions some shorthands). This becomes in effect a universal identifier, like an email address or a social security number.
Deciding to adopt a web page as the user’s handle is an interesting design choice. It’s not hard to see how they fell into this choice. The primary driver of OpenID is a blogging company. Their users all have blogs. Their users are pretty much defined by their blogs. It’s a natural choice. OpenID is unique among the identity systems I’ve looked it, it has only one use case. Leaving a comment on a blog in a way that ties that comment back to the author’s blog.
This isn’t an identity system, like Liberty, designed to support account linking and sophisticated data sharing between mutually suspicious firms on the behalf of thier supicious customers. Since the design’s core feature is a universal identifier for users no privacy advocate is likely to love it. The lack of encryption on the message exchanges is a red flag for large numbers of people.
That said there is a lot to like about OpenID.
The question one needs to ask: Will we have an identity system where user persona is represented by public web pages? Once you accept that that is extremely likely then OpenID becomes a lot more acceptible as a point in the design space of identity systems.
Clearly web pages are better than email addresses or a phone number because those have a obvious operation available on them which is open to abuse. The set of operations on a web page are more limited and more easily configurable.
Users already have a mental model for web pages that is reasonable accurate. This reduces the chance they will just assume more privacy than they are in fact getting.
One very nice aspect about web pages is that we already have a deep suite of tools for empowering users to configure them.
User know, or they ought to know, that web pages are public and durable. So what ever the user publically reveals on the page he uses for his OpenID becomes public information, probably forever.
Nothing about this choice precludes users from having many persona. Nothing about this choice precludes those persona from being reasonably anonymous. It’s a shame that persona management isn’t more carefully designed into OpenID; but at least the mechinisms for it are reasonably transparent for users.
As a choice the decision to adopt the URL of a web page as the corner stone of a public open idenity system seems enivitable.
It’s important to take OpenID on it’s own terms. In it’s heart of hearts it is really just attempting to tie contributed content back to authors; at least a little. That is a more central problem that it might at first appear. OpenID is not trying to solve all the world’s identity problems.


 The VI reference mug, shown at right, is available
The VI reference mug, shown at right, is available